[NS Wk 3] Practical - Firewall Layer 3 Configuration
Practical - Firewall Layer 3 Configuration
This write-up is simply a summary of the practical exercises done in Wk3 without the fluff.
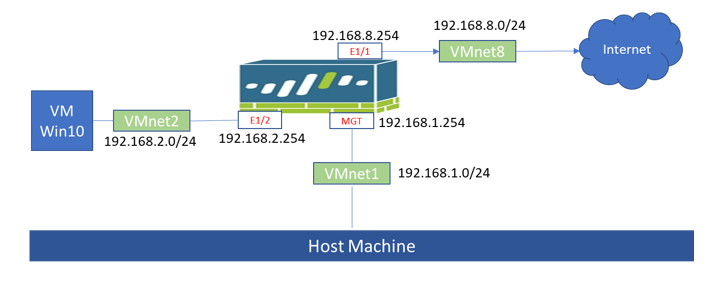
Scenario
Objectives:
- Configure Ethernet Interfaces with Layer 3 Information
- Set up virtual router
- Create security policy
- Configure Source NAT
Configuring Ethernet Interfaces with Layer 3 Information
- On the Firewall GUI, navigate to
Network > Interfaces > Ethernet. - For
ethernet1/1interface (connected to Internet), configure the following:- Ethernet Interface:
- Comment:
outside interface - Interface Type:
Layer3
- Comment:
- Config Tab:
- Virtual Router:
lab-vr - Security Zone:
outside- allows traffic to flow from the outside to the inside
- Virtual Router:
- Advanced Tab:
- Management Profile:
ping- allows ping to the interface
- Management Profile:
- Ethernet Interface:
- For
ethernet1/2interface, configure the following:- Ethernet Interface:
- Comment:
inside interface - Interface Type:
Layer3
- Comment:
- Config Tab:
- Virtual Router:
lab-vr - Security Zone:
inside
- Virtual Router:
- Advanced Tab:
- Management Profile:
ping
- Management Profile:
- Ethernet Interface:
Configuring Virtual Router
- On the Firewall GUI, navigate to
Network > Virtual Routers, and click onlab-vr. - Add a new static route:
- Name:
default-route - Destination:
0.0.0.0/0- Default route; specifies that all traffic not defined in routing table should be sent through the virtual router to the next hop IP address - Next Hop IP Address:
192.168.8.2- VMware’s default gateway IP
- Name:
- Commit the changes.
- To verify, go to client VM (VMnet2) and check for IP address obtained via DHCP (E1/2). ping the
firewall’s
ethernet1/2interface IP address. This should work as it is on the same interface. - Client should not be able to ping the firewall’s
ethernet1/1interface IP address as it is on a different interface.
Create Security Policy
- On the Firewall GUI, navigate to
Policies > Security. - Ensure
egress-outsideis enabled. - Client should now be able to ping the firewall’s
ethernet1/1interface IP address as now there is a security policy allowing traffic from the inside to the outside. - Client should not be able to access the Internet as there is no NAT policy configured; traffic cannot flow from host
to communicate through the host’s
ethernet1/1interface.
Recap:
egress-outsidepolicy defines the traffic flow from a source zone/interface to a destination zone/interface.
Configure Source NAT
Refer to Wk3 Notes here for configurations.
This post is licensed under
CC BY 4.0
by the author.